✅ MALWARE - Crab Rave
Writeup by: @goproslowyo
Tags
- hard
Files:
Description
Author: @HuskyHacks
My biologist friend told me that everything eventually evolves into a crab-like form. I don’t know if that’s true but I guess malware authors got a head start on that evolution. To save you some time, I went ahead and found you the 10 hour extended version of Crab Rave on YouTube (https://www.youtube.com/watch?v=-50NdPawLVY). You’ll need it. So, here’s the deal. This one is tough, so we’re giving you a “Choose Your Own Adventure” challenge. Are you super confident with reverse engineering? Try crab_rave_harder.7z. Not so confident with RE? We gave you crab_rave_easier.7z. Both have the same flag. Both do the same thing. If you solve one, you solve both. No matter which one you go with, it will be challenging. You got this. Archive password: infected NOTE, this challenge is based off of a real malware sample. Windows Defender will probably identify it as malicious. It is strongly encouraged you only analyze this inside of a virtual environment separate from any production devices.
Download the file(s) below.
Writeup
This is a Windows DLL file written in Rust. We’ll need to reverse engineer it to figure out what it’s doing.
First we find the call to DLLMain and see that it’s making a call to NtCheckOSArchitecture.
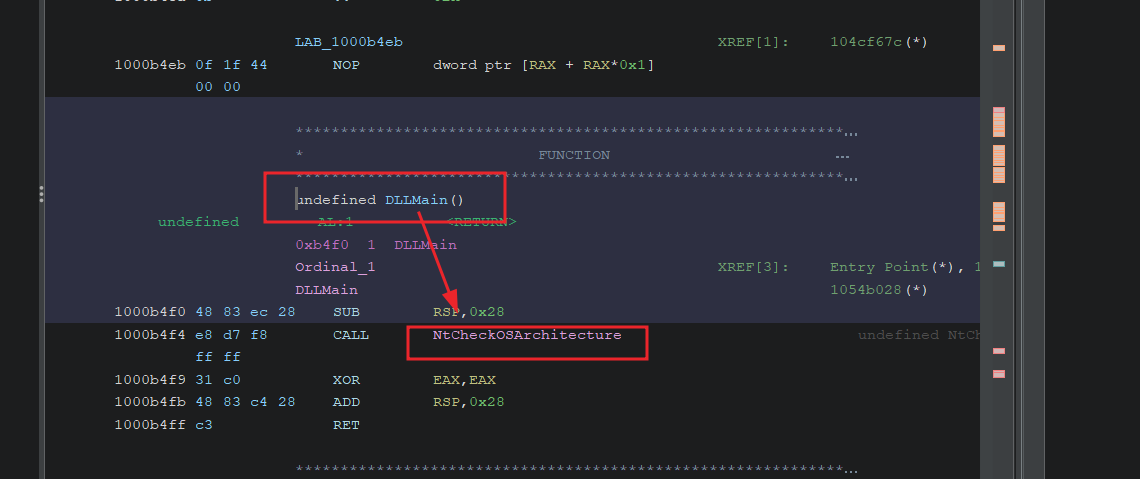
In NtCheckOSArchitecture we see that there are some parameters being passed into a function called decrpyt_bytes that’s apart of the litcrypt rust crate.
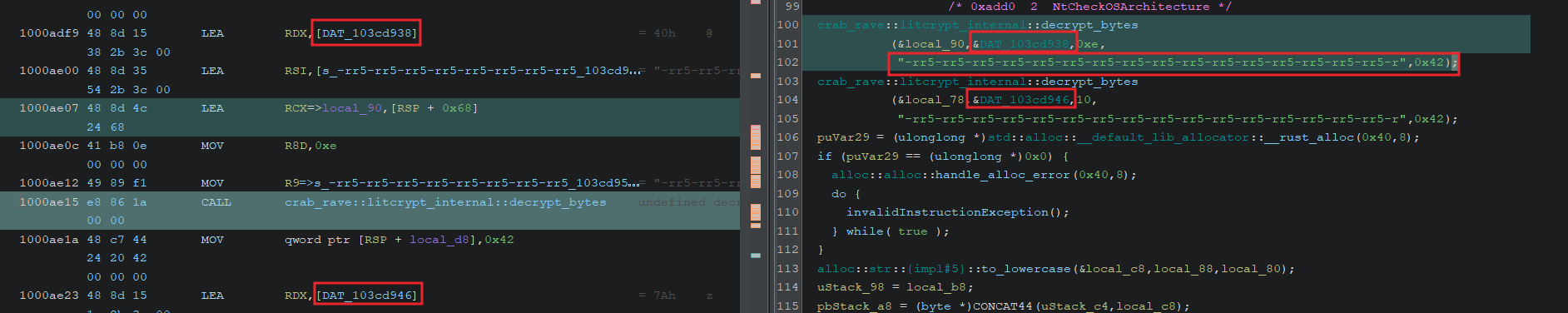
pub fn decrypt_bytes(encrypted: &[u8], encrypt_key: &[u8]) -> String {
let decrypted = xor(&encrypted[..], &encrypt_key);
String::from_utf8(decrypted).unwrap()
}
Nice! It’s just a simple XOR so we should be able to reverse all the XOR’d strings we’re interested in. Let’s pull out all the byte strings and prepare to reverse them. We can select all the bytes, right click, and select Copy Special....
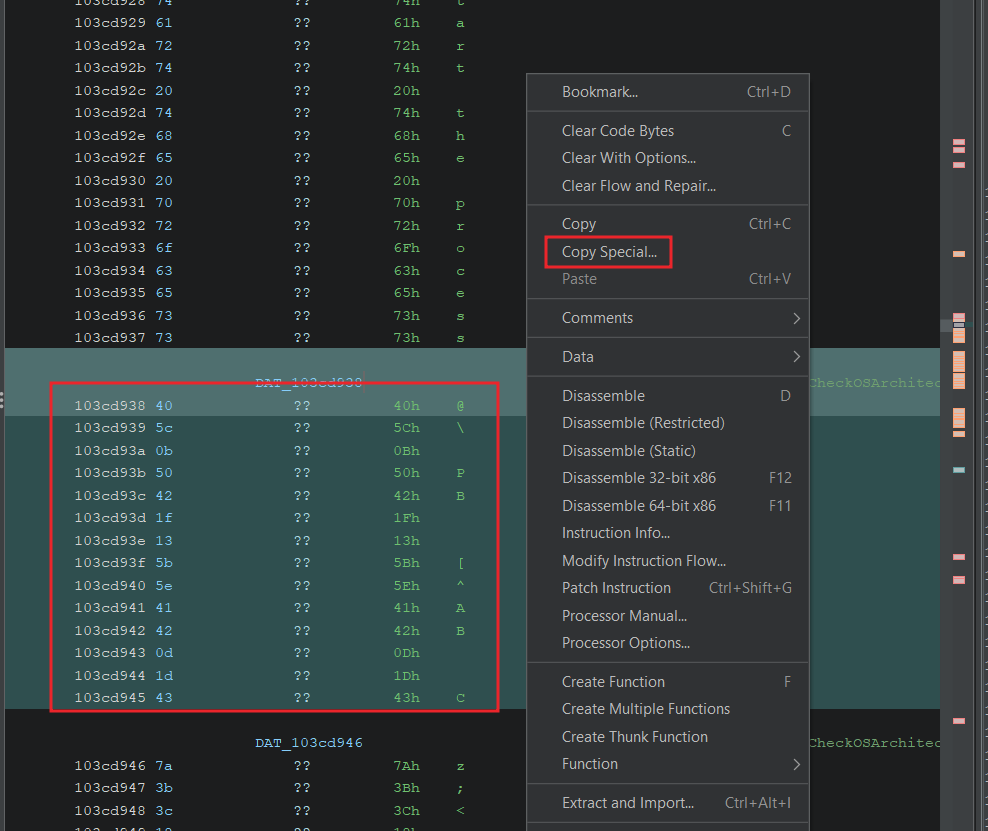
Then choose Byte String or Byte String (No Spaces).
We know the XOR key, shown in the function call, -rr5-rr5-rr5-rr5-rr5-rr5-rr5-rr5-rr5-rr5-rr5-rr5-rr5-rr5-rr5-rr5-r.
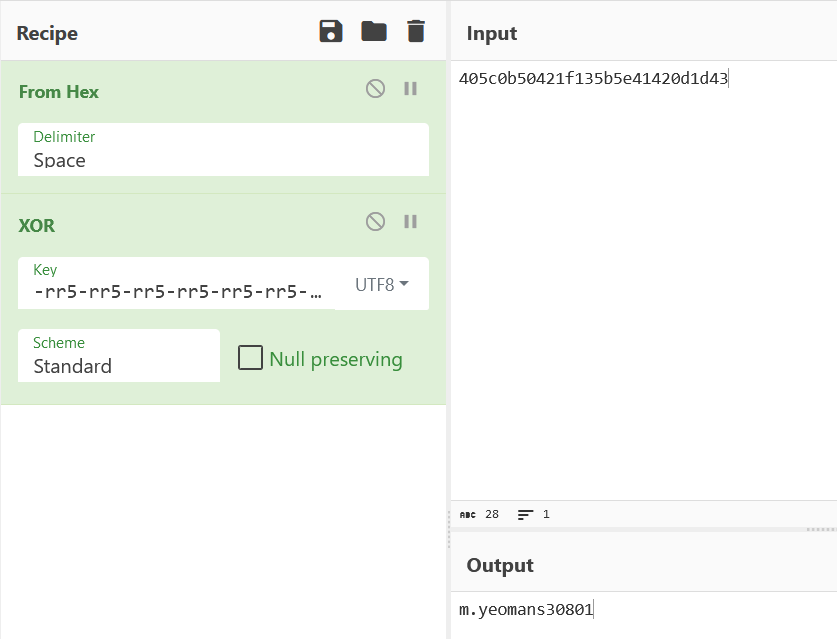
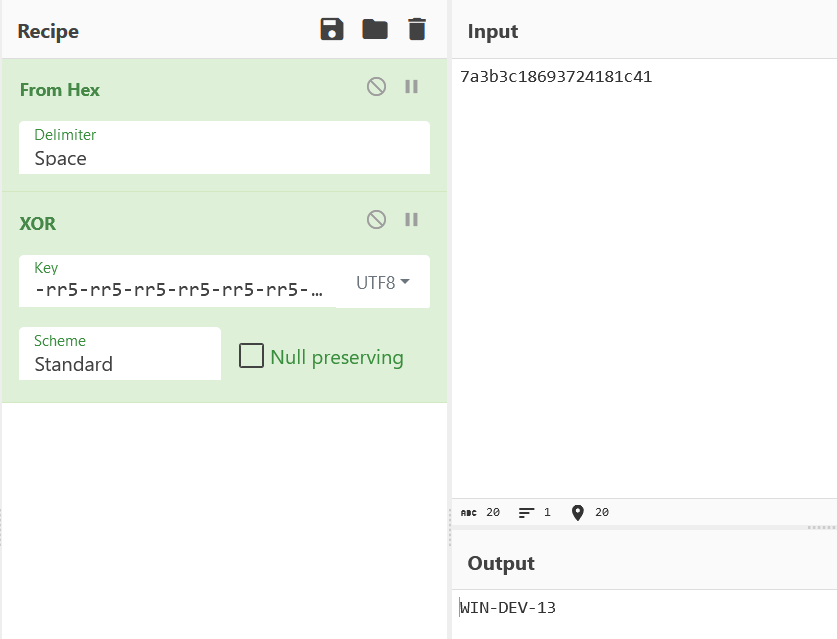
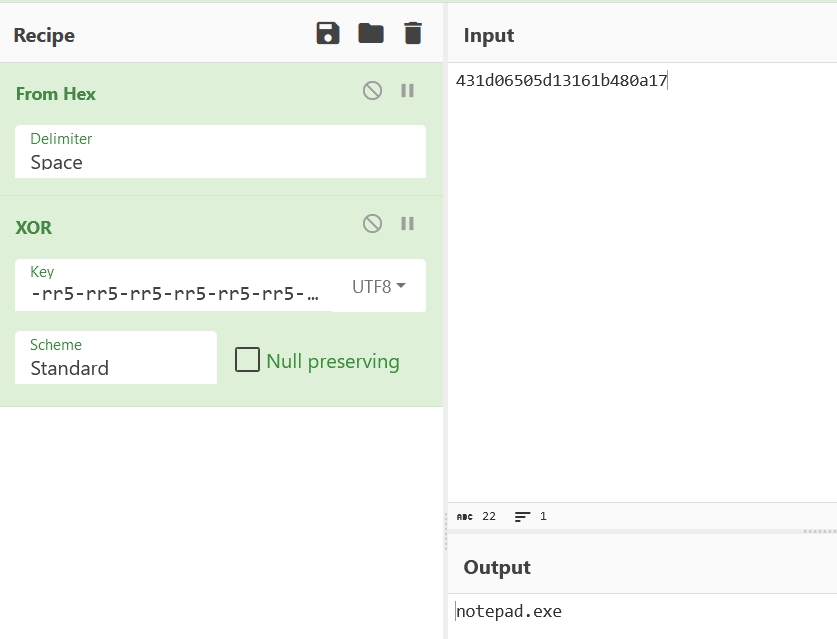
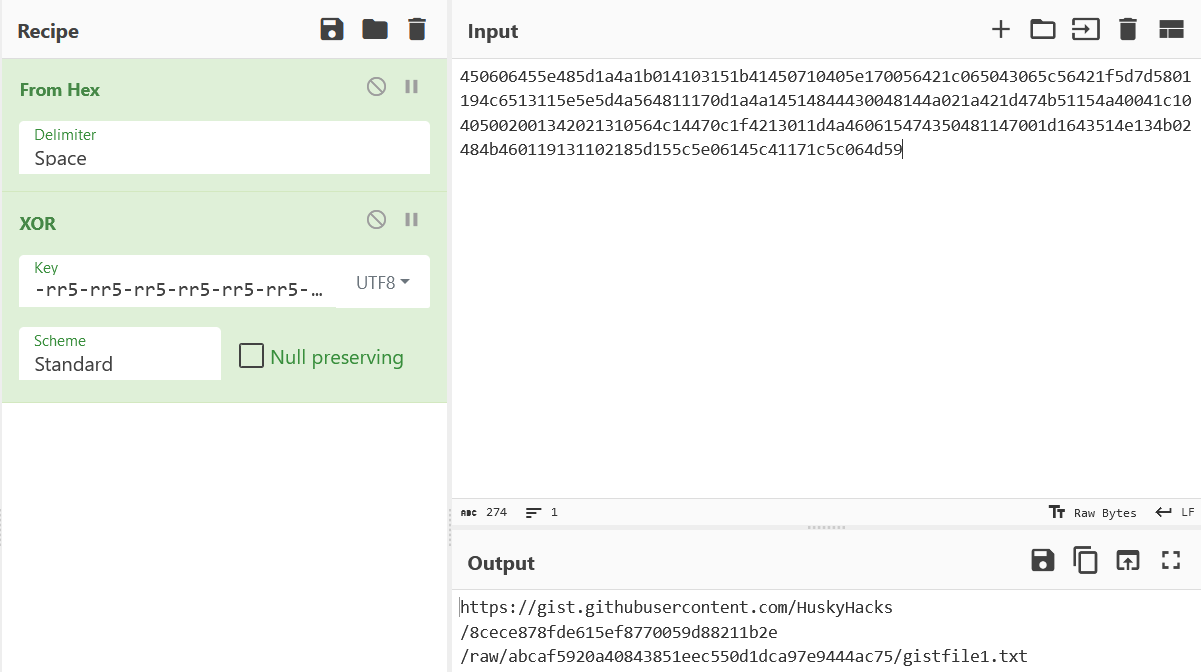
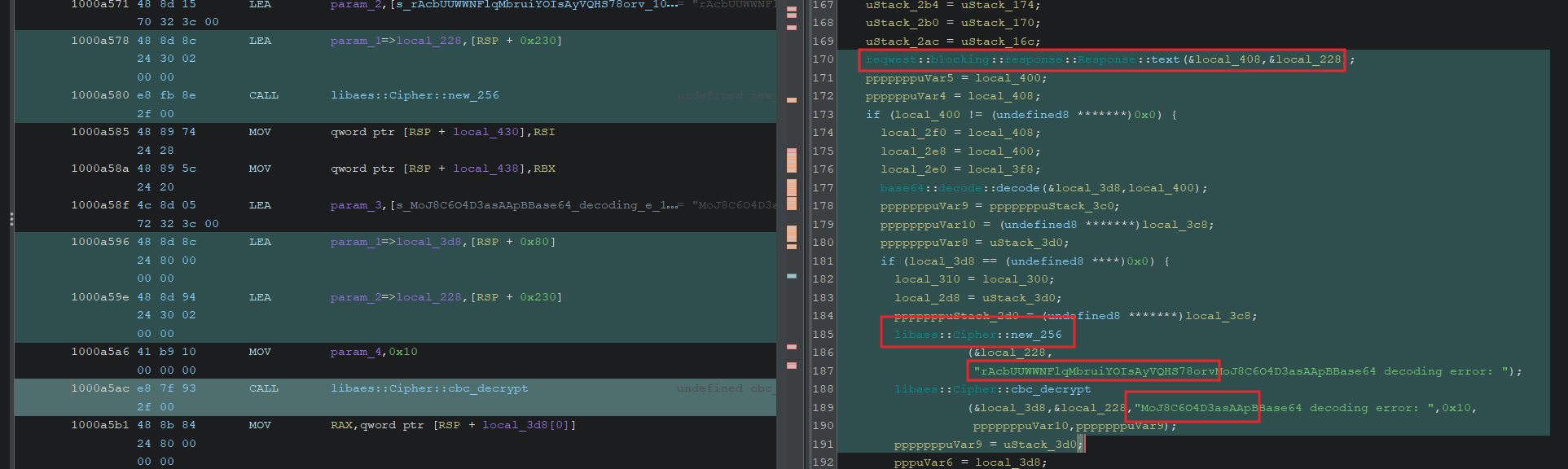
Visiting the Gist URL we find what looks be base64 but decoding it doesn’t give us an intelligible string. If we look deeper at the inject_flag function we can see the base64 decoded text is then passed to AES256 decrypt… aha! We’ve also got to decrypt the string and thankfully we can see the key and IV in the decompiled code as well. So let’s give it a try.
Load the string into CyberChef, base64 decode it, and the run it through the AES decryption tool. Here’s the CyberChef recipe.
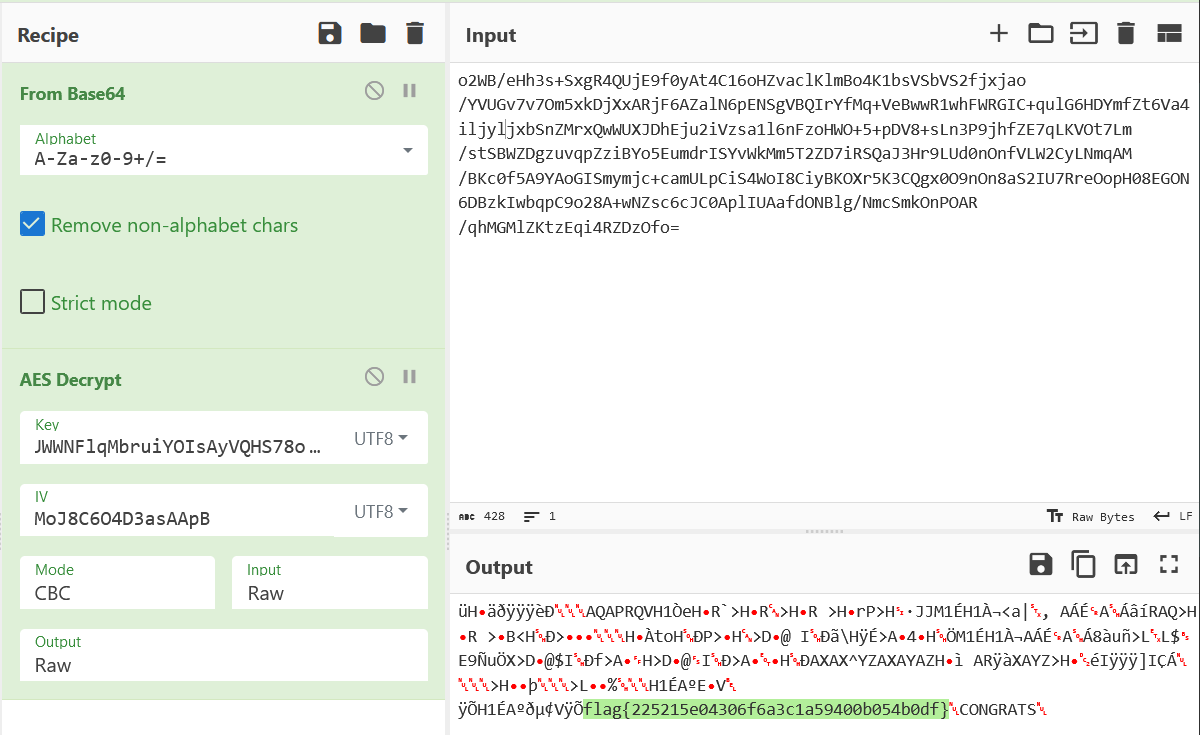
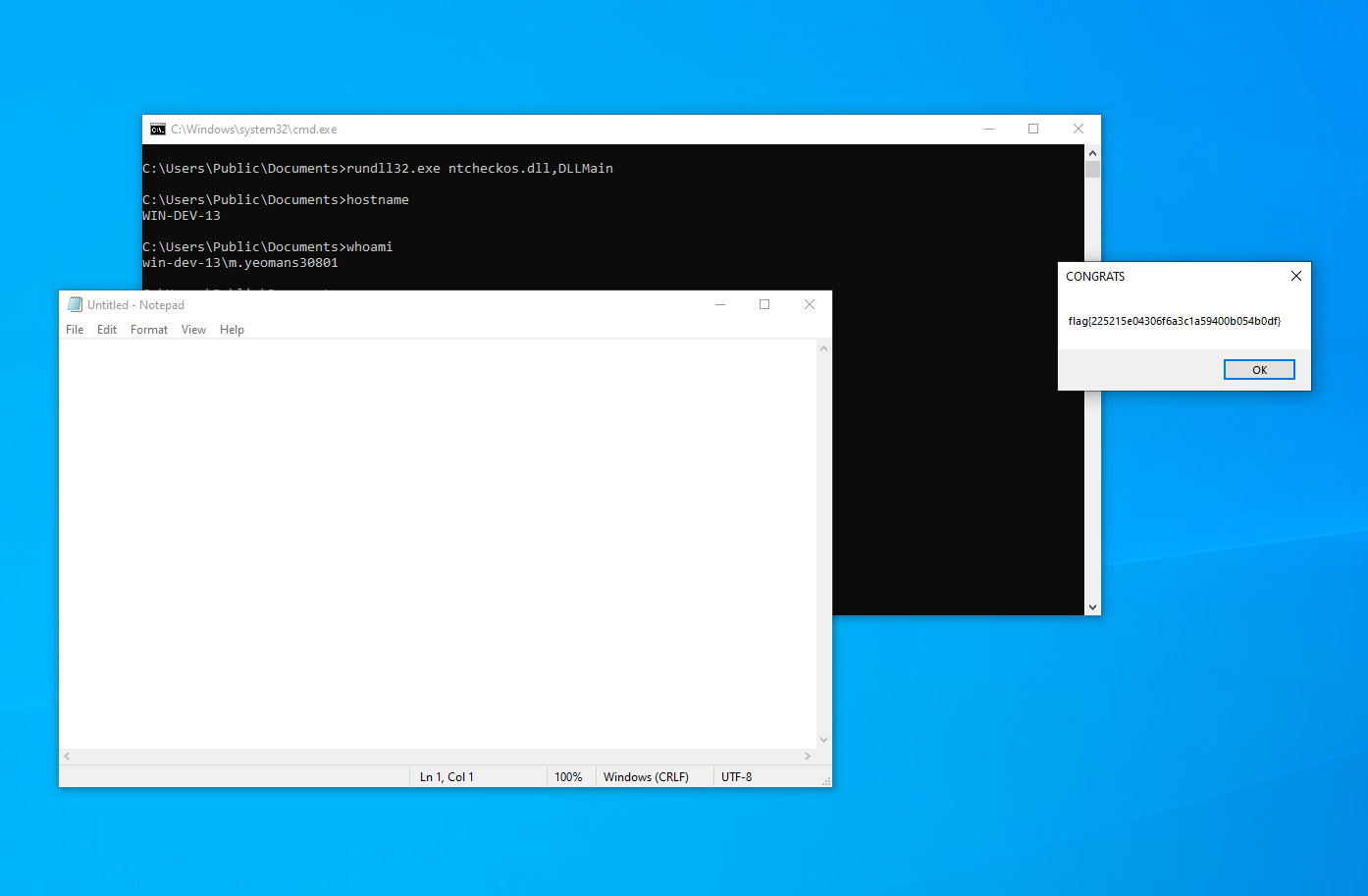
flag{225215e04306f6a3c1a59400b054b0df}
Those strings we decoded earlier, the username and hostname, incidentally, can be used to also get the flag. If you set the hostname, and run the binary as that user, you’ll get a popup with the flag. (Might not be the best approach with real malware ;) unless you’re REALLY trying to analyze it’s behavior.)